|
Getting your Trinity Audio player ready... |
Dive down the rabbit hole and find HIPAA help.
- What Is HIPAA?
- What is HIPAA Compliance?
- What is HIPAA Law?
- What is HIPAA Training?
- How Do You Report HIPAA Violations?
- What are HIPAA Forms?
- 10 HIPAA Security Tips
You have HIPAA problems, we have HIPAA help.
HIPAA is the “Health Insurance Portability And Accountability Act of 1996,” signed into law by President Bill Clinton after Congress approved the Bill.
And this is the HIPAA Help Blueprint 2nd Edition. We’re going to take you down the rabbit hole, but sometimes that’s the best way to survive getting to the other side of the road: just ask the chicken who got ran over a time or two.
With HIPAA, very little is clear; in fact, we’ve been living in the gray area since 1996!
It brought on the gray era in regards to cyberspace, privacy, electronic information, data, archived records, protected health information (PHI), digital documents, Federal Rule enforcement, cyber defenses, new systems of Rule, and the advances of high technology.
HIPAA may be the one topic that continues to cause insomnia for even the most sleep deprived health professionals, and all of their business associates. Deep down, they feel it. They need HIPAA help.
HIPAA. It is complicated, it is complex, it is controversial, and it is cumbersome. It’s a tangled web, but we can help unravel it. It’s a maze, but we will guide you through it.

Let’s start with the good news – you’ve walked through our digital doorway! If HIPAA were a desert, we’d be an underground oasis serving cold water that’s been filtered by reverse osmosis, on tap, with little umbrellas on top.
We are known for producing solar flares in the virtual reality, releasing the forces of the Internet that are buried under congested pathways of misinformation.
Petronella Technology Group (PTG) is home to CEO Craig Petronella, a real-life fountain of HIPAA wisdom. Craig serves as Fractional Chief Information Officer (CIO) and Fractional Chief Information Security Compliance Officer (CISCO) for many small and mid-sized organizations.
He’s the Amazon best-selling author of “How HIPAA Can Crush Your Medical Practice,” as well as books on cybersecurity, hackers, and computer malware.
Next one is on the potential nemesis of HIPAA: the unification of blockchain and artificial intelligence (much more on that below).
That’s our Ace Card, played upfront! We are huge fans of total transparency. Not following? Let’s explore the dark alleys of HIPAA Compliance for a moment- don’t worry, we are known for turning on the lights. When we emerge at the end of the tunnel, you will see a completely different picture- and dusk will have turned to dawn.
Let’s Reverse Engineer HIPAA
Have you ever read terms and conditions forbidding reverse engineering? That’s too bad, because it is so fun. Let’s start at the beginning. We’ve written a very happy ending, but we won’t deprive you of an old-fashioned dramatic story line. Besides, isn’t the journey the reward?
Okay, maybe not for the medical practice here in Raleigh, North Carolina that was recently fined $750,000 for a single HIPAA violation (and some would argue, a minor one). But you know what we mean.
Give us two minutes, and we will give you HIPAA in sixty seconds. With the extra minute, we will summarize the state of the world for you.
We’ll tell you what everyone has gotten all wrong, and why we’ve got the Ace Card.
Actuals and Factuals:
Health Insurance Portability and Accountability Act of 1996
“PUBLIC LAW 104-191104th Congress An Act To amend the Internal Revenue Code of 1986 to improve portability and continuity of health insurance coverage in the group and individual markets, to combat waste, fraud, and abuse in health insurance and health care delivery, to promote the use of medical savings accounts, to improve access to long-term care services and coverage, to simplify the administration of health insurance, and for other purposes.
Be it enacted by the Senate and House of Representatives of the United States of America in Congress assembled, SECTION 1. SHORT TITLE; TABLE OF CONTENTS.(a) SHORT TITLE.–This Act may be cited as the “Health Insurance Portability and Accountability Act of 1996.”
(b) TABLE OF CONTENTS.–The table of contents of this Act is as follows:Sec.1. Short title; table of contents.TITLE I–HEALTH CARE ACCESS, PORTABILITY, AND RENEW ABILITY
But Wait, There’s More…
Or is this the part where we elaborate on HIPAA problems? If you go to www.hhs.gov, you’ll find the U.S. Department of Health and Human Services. They’ve put together a “Combined Regulation Text,” in the form of a PDF. From www.hhs.gov: “This is an unofficial version that presents all the HIPAA regulatory standards in one document.”
And it’s 115 pages long, we might add. Did we mention that it’s the unofficial version? Now that you understand this, we should tell you that, well… There’s still more!
You should review the “Final Privacy Rule” of 2000, which was later amended in 2002. Compliance with this Rule has been required since 2003.
Next, there is the “Final Security Rule” of 2003- compliance with this Rule has been required since 2005. In a nutshell, “this Rule sets national standards for protecting the confidentiality, integrity, and availability of electronic protected health information.”
This is where people are going so, so wrong. But we’ll get back to that when we move on to minute number two.
For now, there’s twenty more seconds of pure federal regulatory fun. You guessed it…there’s more!
Next, there’s the “Enforcement Rule” that provides standards for the enforcement of all the “Administrative Simplification Rules.”
Moving along to the “Final Omnibus Rule” that implements a number of provisions of the HITECH Act to strengthen the privacy and security protections for health information established under HIPAA, finalizing the “Breach Notification Rule.”
Did you notice that we slipped the “HITECH Act” in there? What is HITECH, you ask?
From www.hhs.gov: “The Health Information Technology for Economic and Clinical Health (HITECH) Act, enacted as part of the American Recovery and Reinvestment Act of 2009, was signed into law by Barack Obama on February 17, 2009, to promote the adoption and meaningful use of health information technology.“
It’s HIPAA’s commandeering companion, and those who find themselves buried under its many tentacles of EHR systems are trapped. Those who ignore it have built their houses out of a stack of floppy, wet thumb drives that are plugged into a system USB drive, and linked to a malware-infected UPS (Uninterruptible Power Supply), stored in the internal storage of a corrupted and congested system.
Bad. It’s real bad. It’s one of the many reasons you need HIPAA help.
Office of Civil Rights Letter
This is an OCR audit letter that will make you cringe. Be proactive! Be prepared and be able to respond confidently that your practice CAN pass an audit with flying colors. If you can’t, get HIPAA help.
Sixty Seconds/Second Half
So we didn’t call it bad news, but you probably realize that we just gave it to you. But remember the good news- you’re here, and it’s all about who you know.
And the cards you are dealt. In this case, remember our Ace Card? We pointed out that the “Final Security Rule” was where people were going really wrong. Or should we say, the wrongest? They need HIPAA help!
ALL of the Rules are bringing out the worst in everyone, and we’ve worked with many practices that were sincerely trying to be compliant.
Did you know that encryption is not required by HIPAA?
It’s a great service, that’s not actually required. It’s part of the higher end Google G-Suite plans, the paid version of Google services where Google will sign a Business Associate Agreement (BAA) IF and ONLY IF you properly configure the security controls within the Google ecosystem.
Otherwise, as defined in their terms and conditions, you can still suffer a breach and or steep fines! Microsoft has similar HIPAA compliant packaged in their Microsoft Office 365 E3 packages that include a system called compliance manager, which makes adhering to HIPAA regulations easier in the event of an audit.
Microsoft will also sign a BAA if you properly configure the HIPAA security controls on the Microsoft Office 365 system through compliance manager. This gives you just a little bit of HIPAA help.
Microsoft compliance manager is not a simple system to configure properly. I recommend seeking professional services from a reputable and reliable cybersecurity and compliance firm.
Google sure benefits from medical practices that need to comply with HIPAA regulations. But don’t blindly help them.
You can actually write into your policies and procedures that email is not a supported communication for your practice. This is an area that we specialize in; instead of using insecure email, we use an “encrypted portal system.”
There are different levels with everything, including the internet itself. You’ll find the same is true with security in the cyber realm. But remember, the “Final Security Rule” is the Rule that “sets national standards for protecting the confidentiality, integrity, and availability of electronic protected health information.” Key words: CONFIDENTIALITY, INTEGRITY, AVAILABILITY.
Why are these so key? We live in the Digital Age, and hackers are wreaking havoc. How confidential are your records when a hacker breaches your network?
What’s the integrity of your electronic health information looking like when you’ve got hackers browsing through it? How available are your files when they’re encrypted with ransomware? We don’t like to sugarcoat things.
You’re on the World Wide Web, and so is your business. You are on their turf, and they know the land far better than you do. They have booby traps and land mines everywhere, and you are a sitting duck. They are master duck hunters. But we know how to glitch their game system.
How many ducks do you remember getting when your virtual duck gun was unplugged?
Do you see how this all comes full circle? Craig Petronella, CEO of PTG, is an international authority on BOTH HIPAA AND CYBERSECURITY. Now that’s Wisdom. Check out the video below, where he is interviewed about even webcams being hacked…and you guessed it- that’s a HIPAA violation if it happens to your office!
You can go elsewhere for help with HIPAA, and as you walk in the other direction you will be getting further and further from the light at the end of the tunnel. May we be blunt? Everything, and we mean EVERYTHING, changed on January 1, 1983.
But why, you ask, since HIPAA wasn’t enacted until 1996 (ten years after the Internal Revenue Code of 1986)? Because that’s when the Internet dropped its web on the whole wide world. We won’t sell you a do-it-yourself HIPAA Compliance package for $250, as some will.
They might even be willing to throw in a bottle of snake oil for an extra twenty bucks, and a thermos of their specially brewed kool-aid to quench your thirst for good.
And to cook your goose with the Office of Civil Rights (the auditing arm of HIPAA, between arms 9 and 10 of HIPAA). As you learned in the first sixty seconds, this is a lion’s den. And you’re trapped inside of it, under a spider’s web.
We like to speak the truth; forgive us for being so blunt. Even cybersecurity “experts” come to us for help. We are the Bruce Lee of Cybersecurity, and the Bruce Lee of HIPAA. We are Bruce Lee, SQUARED. We are the Thunder, and we are the Lightning, and this is the Perfect Storm.
Yes, the rules of the game have changed. But, we pulled a genius move:
“Learn the rules of the game; then play better than everyone else.”
-Albert Einstein
Learn More About How We Play, So That You Can’t Lose.
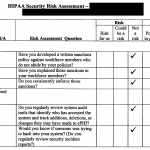
Perform a HIPAA Security Risk Assessment to score your practice as soon as possible! This is a great way to get HIPAA help. You can sign up for one by scrolling to the bottom and visiting our InfusionSoft store. But we’re old fashioned, so you can always call…
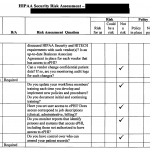
Look at what happened to the practice below when they failed to do a HIPAA Security Risk Assessment. It is a requirement to be done annually as part of the criteria to receive incentives and funding from the government. It’s its own little bit of HIPAA help.
They got the letter below from the OCR outlining the rejection according to meaningful use terms. They needed HIPAA help.
HIPAA Help- What is HIPAA Compliance?
HIPAA compliance is the act of complying with all of the above, and a bit more! It’s virtually impossible unless you enlist an expert for HIPAA help.
Surely you noticed the wording “and other purposes” in the legal description of HIPAA from www.hhs.org? There’s quite a bit of that going on. HIPAA compliance is not violating any of the rules- even the vague and unclear ones.
When you need your back adjusted, you can ask your 17 year old high-school-wrestler nephew to do it, or you can go to a trained Chiropractor.
When you need your car fixed, you can ask your neighbor to do it for you, or you can go to an ASE Certified Mechanic. If you want to be HIPAA compliant, you can do it yourself (correction, you can ATTEMPT to do it yourself- but you won’t be compliant).
Or you can call someone who has 1/10 of the experience with HIPAA that we do, with five times the shady marketing budget. Or you can do it right the first time, and then run your practice with the peace of mind you won’t feel otherwise.If you hire bad help, you’re not going to really get HIPAA help.
What does HIPAA Compliance mean? HIPAA compliance means adhering to the Privacy Rule, the Security Rule, the Final Omnibus Rule, HITECH Act. It almost always means involving an expert in your quest for HIPAA compliance, or spending over a decade learning the loosely defined Rules that we already have a grasp of.
HIPAA Help- What is HIPAA Law?
The Health Insurance Portability and Accountability Act of 1996 was enacted by the 104th United States Congress and signed by President Bill Clinton in 1996. HIPAA was the catalyst for health information going electronic.
It was also the trap for violating privacy and security Rules pertaining to the electronic health records. HITECH added more regulation, and created a big demand for firms that can help with HIPAA, security, privacy, etc.
In summary: The Privacy Rule, a Federal law, gives you rights over your health information and sets rules and limits on who can look at and receive your health information.
The Privacy Rule applies to all forms of individuals’ PHI, whether electronic, written, or oral. The Security Rule is a Federal law that requires security for health information in electronic form. It’s a big reason as to why you need HIPAA help.
HIPAA Help- What is HIPAA Training?
HIPAA requires both covered entities and business associates to provide HIPAA training to members of their staff who handle PHI.
Business associates and any of their subcontractors must also be trained. Anyone who comes into contact with PHI must be trained.
They need to be trained on Policies and Procedures, and you must also have these in writing! You must have a Sanction Policy that outlines how you will handle staff who violate policies.
You can’t use generic policy templates and be compliant. They have to be customized for your practice (we do that too, when we give you HIPAA help).
Staff should understand HIPAA very well. We have a staff training program that is more thorough than what you will find elsewhere.
In addition, we do training updates regularly. HIPAA is never out of sight with us, and so it’s never out of mind.
How often is HIPAA training required?
The HIPAA training requirements are more guidance than law – suggesting training should be provided periodically and when certain events occur. Again, more vague language.
We suggest comprehensive yearly training, with ongoing training on a monthly basis. It wouldn’t hurt to throw in weekly “pop quizzes” and “phishing email tests” as a precaution, and we offer these as well. Since the law is vague, the more you do to show due diligence in compliance, the better off you should fare.
HIPAA Help – How Do You Report HIPAA Violations?
To report a HIPAA violation, you email or call the Office of Civil Rights. From their website: You may file a complaint for yourself, your organization, or for someone else.
If you need help filing a civil rights, conscience and religious freedom, or health information privacy complaint, please email OCR at [email protected] or call 1-800-368-1019.
Also, there is a portal you can use. https://ocrportal.hhs.gov/ocr/cp/complaint_frontpage.jsf But what are HIPAA violations?
HIPAA Violations are any violation of any of the policies or Rules described in the legal acts of HIPAA and HITECH.
They could be related to breaches of confidentiality, breaches of integrity, breaches of privacy, breaches of security, lack of availability of electronic health records, compromise of PHI, and so much more. Another reason why you should get HIPAA help ASAP.
Remember this is a lion’s den. A gray one. You’re under a spider’s web. If under the web lies a spider or maybe an Artificial Intelligence bot, HIPAA is a huge centipede sitting on top of it. It’s all quite a mess. You really do need help with all of this.
HIPAA Help- What are HIPAA Forms?
Policies and Procedures need to be in place, and all staff need to be familiar with them. There is a Sanction Policy, a BYOD policy, there are consent forms, and more.
You shouldn’t do these yourself. We worked with a HIPAA Attorney to create forms that we can customize for our clients. Again, the laws are loose and vague.
Due diligence, and being able to prove it, is how you avoid hefty fines and major damage to your business continuity.
Summary of the HIPAA Security Rule from HHS.ORG:
This is a summary of key elements of the Security Rule including who is covered, what information is protected, and what safeguards must be in place to ensure appropriate protection of electronic PHI (ePHI). Because it is an overview of the Security Rule, it does not address every detail of each provision. (YIKES!)
HIPAA Help- Introduction to HIPAA Recap
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) required the Secretary of the U.S. Department of Health and Human Services (HHS) to develop regulations protecting the privacy and security of certain health information.1 To fulfill this requirement, HHS published what are commonly known as the HIPAA Privacy Rule and the HIPAA Security Rule.
The Privacy Rule, or Standards for Privacy of Individually Identifiable Health Information, establishes national standards for the protection of certain health information. The Security Standards for the Protection of Electronic Protected Health Information (the Security Rule) establish a national set of security standards for protecting certain health information that is held or transferred in electronic form.
The Security Rule operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards that organizations called “covered entities” must put in place to secure individuals’ ePHI. Within HHS, the Office for Civil Rights (OCR) has responsibility for enforcing the Privacy and Security Rules with voluntary compliance activities and civil money penalties.
Prior to HIPAA, no generally accepted set of security standards or general requirements for protecting health information existed in the health care industry.
At the same time, new technologies were evolving, and the health care industry began to move away from paper processes and rely more heavily on the use of electronic information systems to pay claims, answer eligibility questions, provide health information and conduct a host of other administrative and clinically based functions.
Today, providers are using clinical applications such as computerized physician order entry (CPOE) systems, electronic health records (EHR), and radiology, pharmacy, and laboratory systems. Health plans are providing access to claims and care management, as well as member self-service applications.
While this means that the medical workforce can be more mobile and efficient (i.e., physicians can check patient records and test results from wherever they are), the rise in the adoption rate of these technologies increases the potential security risks.
(It’s also strengthening the role of artificial intelligence… HIPAA is a paperwork dump on top of it!)
A major goal of the Security Rule is to protect the privacy of individuals’ health information while allowing covered entities to adopt new technologies to improve the quality and efficiency of patient care.
Given that the health care marketplace is diverse, the Security Rule is designed to be flexible and scalable so a covered entity can implement policies, procedures, and technologies that are appropriate for the entity’s particular size, organizational structure, and risks to consumers’ ePHI. Flexibility in HIPAA rules means that every CE and BA needs HIPAA help.
HIPAA Help- Checklist: 10 Point HIPAA Security Tips
- Have you ever had a HIPAA security risk assessment done?
- Have you ever had a penetration test (Pen Test) done?
- Are you using SSL website encryption, email encryption, hard disk encryption AND keystroke encryption?
- Are you using a security solution that stops all persistent malware and ransomware threats from being able to write to the hard disk drive?\
- Are you aware of all of the important policies and procedures you need to have in place? Do you have all of these policies and procedures: Written Information Security Policy, Disaster Recovery Plan, Sanction Policy, Emergency Operations Policy, Network Security Policy, Access Control Policy, Computer Use Policy, Equipment Disposal Policy, Termination Policy, Security Incident Response, Facility Security Plan, and BYOD Policy?
- Do you have a BAA in place with all of your vendors? Make sure you have a business associate agreement or BAA in place with all of your vendors. I can’t stress this enough. If you have just one vendor that you missed, it could cost your practice huge fines. A local medical practice just got hit with $750,000 in fines for not having a BAA in place with a third-party x-ray company.
- Do you have privacy screens on all of your computers, laptops and devices?
- Do you lock up any physical files that contain Patient Health Information (PHI)?
- Does your computer screen timeout after 3 minutes or less with a password prompt?
- Do you have the passcode and encryption features on all mobile devices, tablets iPhones, droid devices, etc. enabled?
A Glimpse of Light
As we mentioned, CEO Craig Petronella is the Amazon Bestselling Author of “How HIPAA Can Crush Your Medical Practice.” The book is available on Amazon; let’s take a sneak peek inside to get an overview of content:
Section 1……Introduction: HIPAA Can Hurt you (AND IT WILL)
Chapter 1……Are you in the HIPAA Crosshairs? Chances are, yes you are. If you are human, operating a medical practice, and not a HIPAA law expert. They have assessed fines in EXCESS of $2 million dollars. THERE IS NO TIME TO WASTE. IT’S TIME TO WAKE UP AND COME TO THE LIGHT.
Chapter 2……What does it take to comply with HIPAA? Just short of your firstborn child, really.
Chapter 3……Why is failure to comply so serious? Audits are picking up- the OCR has formally announced this. IF YOU ARE GOING TO SAVE YOURSELF, YOU MUST DO IT NOW.
Section II……Introduction: HIPAA Violations Can Occur Against Your Will (NOT GOOD!)
Chapter 4……How do breaches happen? Ah, let us count the ways!!
Chapter 5……What cyber threats do you face? All of the above! Malware, ransomware, zero-day threats.
Chapter 6……Why must security maintenance be active and ongoing? Have you ever painted a constantly changing landscape?
Section III……Introduction: Your Data Can Be Kidnapped (DEFINE DATA! One is just a DATUM)!
Chapter 7……What Exactly is Ransomware? We won’t say that it seems to be what is taking one U.S. city hostage at a time, but some would! This is a REAL threat.
Chapter 8……How would ransomware ruin my day? Again, let us count the ways! Just ask the City of Baltimore!
Chapter 9……How can I prevent a ransomware attack? Our 22 layers of woven security solutions are the anti-threat.It’s the only way we know of to break free of hostage threats!
Section IV……Introduction: You can protect yourself. Did we mention our 22 layers of (mostly patented) security technologies?
Chapter 10……What preventative measures can you take?
Chapter 11……Why is having a quality IT provider so important? It’s hard to believe that in 2019, anyone would still ask this question! World War III is on the World Wide Web, and you are being summoned…whether you like it or not!
Chapter 12……How can you choose the best IT provider for you? Well, you’re on our page- so you’re off to a good start. In the age of information, Wisdom is the key. Wisdom is perfect HIPAA help.
Four Pillars of IT Success Analysis
Actual Disasters the Four Pillars could (or did) prevent
Appendix
Did Someone Say Artificial Intelligence?
It is symbolic that we end with artificial intelligence or AI. Wouldn’t wisdom count as artificial intelligence? You aren’t born with it. You live, and you learn. You acquire wisdom.
That’s our Ace Card.
We leverage advanced artificial intelligence in almost every part of our business model. AI gives us super powers and allows us to analyze mass amounts of information; security logs, emails, etc. looking for patterns so we can sift and sort faster.
We let AI do our heavy lifting so that when security issues and patterns are found, our engineers can respond fast. We have acquired much wisdom, and we are now a force to reckon with!
Artificial intelligence is leveling the playing field. Hospitals, doctors, surgeons and teams of medical professionals leverage AI technology to help perform assessments on the health of their patients. Artificial intelligence, machine learning and deep learning software can arm medical professionals with powerful tools to scan volumes of data in seconds screening for diseases such as cancer.
New technology such as Health Passport technology that leverages Blockchain technology will give patients back the control over their medical records. At the touch of a button, patients can be in full control of who sees their electronic health records, for what reason, and for how long.
Don’t fear AI. It will make us all super-humans, and we can be victors even as we slump around in the gray area. Machines are being trained to screen blood for diseases across a mind-blowing number of samples.
Artificial Intelligence is Wisdom, and it will decide the winner of World War III.
You can’t use artificial intelligence safely without the proper cybersecurity controls in place. Or at least you really, really shouldn’t. For the sake of the whole world.
You can’t be HIPAA compliant without the proper cybersecurity controls in place. Do you know of anyone else who offers our custom 22 layered approach? We don’t. And we’ve searched. It seems that we are charged with the quest of saving the world from the gray area of HIPAA.
Let WISDOM be your guide.
We assure you, it’s the perfect HIPAA helper.
Secure Hosting, Managed Security Services and HIPAA Security Controls: HIPAA Help
(Examples as of July 12, 2019; subject to change at any time; pricing varies)
- PTG WorkSpaces: Secure hosted desktop workspace.
- PTG Unhackable Server Encryption: Patented digital prophylaxis for servers.
- PTG Unhackable Maintenance: Proactive daily updates to operating systems, browsers and third-party applications.
- PTG Upstream Bandwidth: from PTG Cloud to your office. Up to 100 GB per month total bandwidth.
- Microsoft Windows Licenses for server-side hosting.
- Vmware Virtualization for hyper-visor layer.
- PTG Business Continuity Level I: Full backup on all hosted / cloud data within secure HIPAA/HITRUST, SOC 2 Type II, Raleigh, NC data center.
- PTG Cloud file share (super secure Dropbox like service), up to 50Gb.
- PTG Domain Controller for User Active Directory, configured to your practice.
- PTG Dynamic Resource Allocation: Dynamic expansion to 16GB RAM and 2 CPUs to ensure quality user experience.
- PTG Endpoint Antivirus: Real-time attack monitoring and defense of end-user computers from server-side prophylaxis (compliments existing anti-virus packages).
- PTG Firewall: router & access logging and monitoring, required for HIPAA compliance.
- PTG Remote-access VPN: encryption of all user access from public WiFi and open networks.
- PTG Technical Support of Secure Hosting – 24x7x365 via phone, email, or ticket for hosting related issues.
- Does not cover IT user support inhouse or personal-use computers, laptops, smartphones or wearables.
- PTG Multi-factor User Authentication, configured with user training guide and HIPAA Policies.
- Microsoft Office 365 E3: HIPAA compliant, includes Business Associate Agreement (BAA) from Microsoft.
- PTG Unhackable Website: Patented digital prophylaxis for your Website, blogs and related media. Transport Layer Security.
- Website content backup. Visitor Geo-blocking. Distributed Denial of Service (DDOS) protection.
- Pure HIPAA Help!
Get HIPAA Help! PTG Managed Services:
- PTG Encrypted DNS: Encrypted Domain Name Service (eDNS) – Encrypts website traffic, automatically blocks malicious websites
- PTG Encrytped Password Management for all devices with monitoring, multi-factor authentication, hardware token, 100+ policies and procedures.
- This includes the use of a hardware token, eliminating the vulnerability associated with remembering and inputting passwords.
- PTG Endpoints Force field: Security controls configured against HIPAA Policies for computers, smart phones, phone systems.
- NOTE: This entails a weekly protocol for validating that your HIPAA mandated controls are functioning; includes audit trail and the ability to provide a report of compliance.
- PTG Unhackable Email Encryption: Patented digital prophylaxis for all email exchanges.
- PTG Threat Landscape Management: Proactive monitoring of threat landscape and direct surveillance of malicious penetration attempts, logging and maintenance, across your entire IT infrastructure.
- PTG Website Forcefield: Reconfigure WordPress (or other CMS), install firewall, malware scanner, IP address blocking.
- PTG Unhackable Maintenance: Proactive daily updates to operating systems, browsers and third-party applications.
- PTG Unhackable System Encryption: Patented digital prophylaxis for desktop laptop, and mobile devices.
- PTG Unhackable MS Office 365: Patented digital prophylaxis. Maximum security hardening.
- Notifications for any unusual behavior (changes to mailboxes, forwarding, rules, logins, etc.) as well as implementation and monitoring of the two-factor user authentication.
- PTG Office 365 Email 100% Uptime: Patented digital prophylaxis that guarantees that your users will have send/receive email capabilities, Addresses downtime of Office 365.
- PTG Unhackable Endpoint 100GB Backups: Daily virus-free backups of end-user computers (phones and tablets not covered).
- PTG Unhackable 50gb Cloud Storage: Secure Replacement for Microsoft OneDrive: Enterprise file sync and sharing. Improved levels permissions, files control, reporting, auditing. Remote wipes of stolen or lost computers or smartphones.
- PTG HIPAA Compliant Phone Service with Polycom VVX 350 phones, signed BAA and monitoring as required by HIPAA.
- PTG Unhackable Virtual Private Network: Patented digital prophylaxis for remote access from any public network. Secure Use of Public WiFi. Tunneling: users may use any WiFi network with assured privacy. Encrypted access: Defeats WiFi network sniffing and capture of user credentials.
- PTG CloudUTM: Enterprise Managed Firewall with the ability to support fail-over. New faster/more reliable firewall equipment with lifetime warranty. If equipment fails, we replace it FREE. Segmentation. More reliable and with multiple, secure, network segments. State-of-the-art security and filtering. Granular control of the network by using dedicated equipment paired with our CloudUTM with reduced latency. Block categories of web traffic and run detailed reports.
- Pure HIPAA help!
Get HIPAA Help! PTG Compliance Services:
- PTG HIPAA Security Risk Assessment: Annual assessment of practice as required by HIPAA.
- PTG HIPAA Bootcamp: 12 Self-directed online training videos and activities with PTG Quizes and worksheets graded for each module.
- Monthly fee provides HIPAA Training updates and 24/7 support for the learning management system.
- PTG HIPAA Policy Kit: Boiler plate policies and procedures customized to your practice per HIPAA requirements.
- PTG HIPAA Documentation Service: Customization of Policies and Procedures that comply with HIPAA requirements.
- PTG Website Policy Kit: Boiler plate policies and procedures customized to your practice per HIPAA requirements.
- Cyber Insurance for HIPAA Breach and Fine Expenses: $250,000 policy.
- PTG Security Awareness User Training and Certification: Self-directed online training videos and activites with PTG Certificate of Compliance for each employee.
- PTG User Training and Certification for HIPAA: Self-directed online training videos and activites with PTG Certificate of Compliance for each employee.
- PTG Business Associate Agreement (BAA) Service: Customization of your BA agreements (for legal attestation).
- PTG Simulated Phishing Campaigns: A phishing test is where deceptive emails, similar to malicious emails, are sent by an organization to their own staff to gauge their response to phishing and similar email attacks..
- PTG Employee Vulnerability Assessment: Find out which employee(s) are at high risk to potentially cause a data breach!.
- PTG Unhackable Newsletter: Regular updates about the current IT security threats, cybercrime tactics, cyberheist schemes, social engineering scams and ransomware attacks.
- Includes hints and tips to help you block hackers that could cause HIPAA breach.
- PTG Dark Web Monitoring: Also known as cyber monitoring, is an identity theft prevention product that enables you to monitor your identity information on the dark web, and receive notifications if your information is found online.
- PTG Weekly Micro-Training Video & Quiz.
- PTG Situation Awareness & Reporting: Monthly review of Proactive Cybersafety activities and counter measures.
- PTG Breach Reporting: In the event of the actual or suspected breach of PHI/PII, PTG Breach Reporting notifies Federal and State regulatory authorities and consumers as mandated. Your call to PTG about potential privacy breach will initiate an immediate evaluation of your incident; PTG will determine where or not to notify authorities and consumers. PTG will file the necessary breach reports on your behalf, leaving it to you notify your patients and affiliates with inputs and talking points from PTG.
- PTG Incidence Reports for OCR: Preparation of report of findings and remediation’s (where applicable) for submission to Office of Civil Rights of US Dept of HHS.
- Pure HIPAA help!
Get HIPAA HELP! CALL THE EXPERTS: